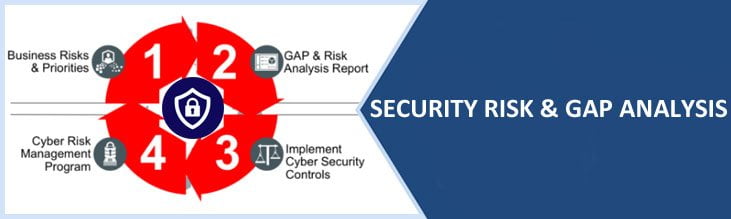
A gap analysis is a study to work out the distinction between the present state of data security and its ideal or optimum state of security. Gap analysis is a very important part of the business continuity planning and is additionally a kind of risk assessment.
Security Risk is a function of the values of threat, consequence, and vulnerability. Addressing the quantity and evolution of cyber attacks is daunting for even the foremost security-forward IT groups. It needs an in-depth understanding of structure risks and vulnerabilities, similarly as current threats and therefore the best policies and technologies for addressing them. Solely by understanding their risks organizations use technologies and techniques that matter most.
We provide with a comprehensive review and analysis of the present state of your security for your infrastructure, network, information and users likewise as your operational processes, procedures, and gaps in coverage. Utilizing the most recent in technology, connected with our security expertise, we offer manual and automatic configuration reviews on the present data infrastructure and network devices. We tend to review potential net exposures among web applications like input validation, service and application configuration, and authentication vulnerabilities.
Our secure and complete analysis using result-oriented strategies whereas adhering to the rules can make sure that your regular processes run seamlessly.
Security and gap analysis will be performed by efficient strategies like a probing questionnaire where the subsequent queries are also included:
1 Are the servers placed in a very secure, restricted space (computer room)
2 Is the pc area restricted to licensed personnel
3 Does the enterprise have biometric access control to manage entry and exit
4 How much-unauthorized access to the system was created and recorded
5 Were unauthorized access to the system investigated
By analyzing the corporate setup, worker credentials and evaluating access and control, the security method is streamlined to prevent loss of information by any means.